Following the subject of this here previous post, I’ll discuss here a possible configuration process for DHCP reliant networks, with firewalls between segments.
The Windows Distributed Transaction Coordinator performs its communication using RPC communication, which by default means it requires 135 port and a set of dynamic ports above 1024.
A dynamic set of ports with no well-known range is not a best practice for network security. Given that, it’s not a question of just asking the firewall administrator to open the default ports. We’ll first configure a port range on the DTC service of the target machines.
On one of the hosts to configure:
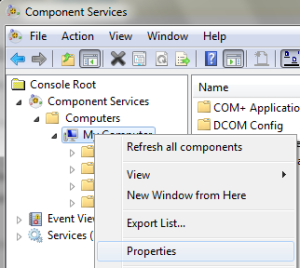
- open the Windows Menu > Administrative Tools > Component Services;
- Drill-down to “My Computer”, then select “Properties” from the mouse context menu;
- Select the “Default Protocols” tab. There should be a “Connection Oriented TCP/IP” item; Press the “Properties” button.
- Press the “Add” button and type in a suitable range like “50000-50200”. This means DTC will use RPC thru ports 50000 to 50200.
Press OK on all windows and restart the server to assure it assumes the newly configured range.
Please note that this configuration has to be done on ALL hosts participating on the distributed transaction. If a given scenario has two separate MSSQL Server hosts and two more application servers, all four machines must have the port range configured on the DTC service configuration.
This step configured the port range for MSDTC on the target hosts. The next step is to request the firewall administrator to open the following ports between the two networks:
- 135: fixed standard port for RPC
- 50000-50200: the range we configured on the example. Could be another given range.
Besides the network firewalls, each hosts own Windows firewall configuration must be edited to allow the connections thru the newly configured port range. To do this, on each host, open the “Windows Firewall with Advanced Security” utility. If hints on that are needed, there’s this article on Technet.
Talking about distributed transactions over the network, it’s obvious TCP/IP communications ar involved. Consequently, this channel has to be enabled on the local DTC.
- open the Windows Menu > Administrative Tools > Component Services;
- Drill-down to “My Computer \ Distributed Transaction Coordinator \ Local DTC”, then select “Properties” from the mouse context menu;
- Select the “Security” tab. The following options need to be checked: Network DTC Access, Allow Remote Clients, Allow Remote Administration
- Still on the same window, on the Transaction Manager Communication: Allow Inbound, Allow Outbound, No Authentication Required
- Check the Enable XA Transactions, uncheck the SNA LU option if you’re no using legacy systems.

Press OK on all windows. It should be all done. This scenario still relies on dynamically assigned IP addresses and windows network architecture with WINS servers.
On the next and final post of the series, I’ll consider a worst case scenario:
- static addressing of the hosts
- no naming servers available
- packet broadcast disabled
- firewall between application hosts and database hosts
It should be relatively interesting since everything is configured manually and it’s a not so uncommon scenario for highly secured, tightly managed networks.



Pingback: Distributed Transactions on Windows 2008 Systems – III | Rambles on Technology